In the fast-evolving landscape of smart offices, ensuring the security of your network is paramount. From the potential risks of cyber threats to the importance of encryption and access control, this guide delves into the key strategies for maintaining a safe and protected smart office environment.
Let's explore the essential steps to safeguarding your office network in this digital age.
Importance of Securing a Smart Office Network
In today's digital age, securing a smart office network is of paramount importance to safeguard sensitive data and ensure smooth operations. The consequences of neglecting network security can be severe and far-reaching.
Potential Risks of an Unsecured Smart Office Network
- Unauthorized access: Hackers can exploit vulnerabilities in an unsecured network to gain access to confidential information, compromising the integrity of the entire system.
- Data breaches: A breach in security can result in the exposure of sensitive data, leading to financial losses, legal implications, and damage to the company's reputation.
- Malware attacks: Without proper security measures, smart devices within the office network are susceptible to malware infections, causing disruptions in operations and potential data loss.
Consequences of a Security Breach in a Smart Office Environment
- Financial losses: The cost of recovering from a security breach, including legal fees, fines, and compensation to affected parties, can be substantial.
- Reputation damage: A security breach can erode trust among clients, partners, and employees, impacting the company's reputation and credibility in the market.
- Operational disruptions: In the event of a breach, the office network may experience downtime, leading to productivity losses and delays in delivering services.
Real-life Incidents Related to Smart Office Network Vulnerabilities
One notable incident involved a smart office network being compromised by ransomware, resulting in the encryption of critical files and a demand for payment to unlock them. This incident caused significant disruptions and financial losses for the affected company.
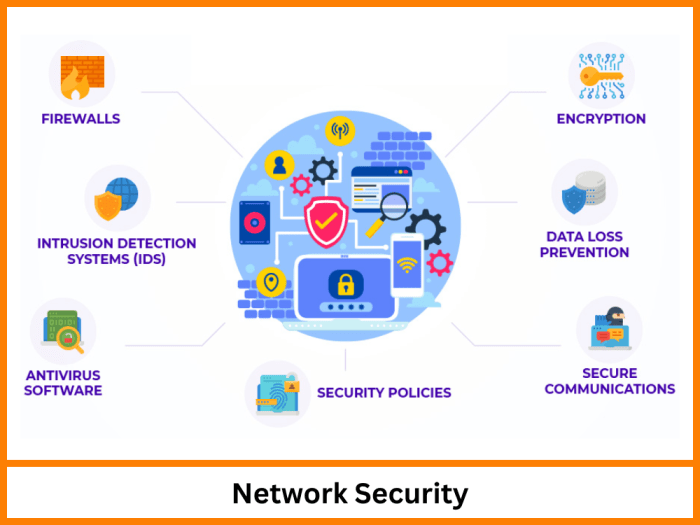
Network Security Best Practices for Smart Offices
Securing a smart office network involves implementing basic principles to protect devices and data from potential threats.
The Role of Encryption
Encryption plays a crucial role in safeguarding smart office devices and data by encoding information in a way that only authorized parties can access it.
Regular Software Updates and Patch Management
Regular software updates and patch management are essential for network security in smart offices. These updates help to fix vulnerabilities and strengthen the overall security of the network.
Securing IoT Devices in a Smart Office Setting
IoT devices play a crucial role in a smart office environment, enabling automation and connectivity like never before. However, these devices also introduce unique security challenges that must be addressed to protect the network from potential vulnerabilities.
Challenges Posed by IoT Devices
IoT devices often come with limited security features, making them easy targets for cyber attacks. Their constant connection to the internet and the office network increases the risk of unauthorized access and data breaches. Moreover, the sheer number of IoT devices present in a smart office creates a larger attack surface for cyber threats.
Tips for Securing IoT Devices
- Change default passwords: Always change the default passwords on IoT devices to strong, unique passwords to prevent unauthorized access.
- Keep devices updated: Regularly update the firmware and software of IoT devices to patch any known vulnerabilities.
- Enable encryption: Ensure that data transmitted between IoT devices and the network is encrypted to protect sensitive information.
- Implement network segmentation: Segregate IoT devices into separate networks to limit the impact of a security breach and prevent lateral movement by attackers.
- Monitor device activity: Continuously monitor the network for any unusual activity or unauthorized access attempts from IoT devices.
Network Segmentation and IoT Device Security
Network segmentation involves dividing a network into smaller subnetworks to enhance security and control access. In the context of IoT devices, implementing network segmentation can help isolate these devices from critical systems and data, reducing the potential damage of a security breach.
By creating separate segments for IoT devices, organizations can apply specific security measures tailored to the unique requirements of these devices, effectively minimizing the risk of a widespread cyber attack.
Implementing Access Control Measures
Access control is a crucial aspect of smart office network security, as it helps in regulating and managing who can access certain resources or areas within the network. By implementing access control measures, organizations can prevent unauthorized access to sensitive data and reduce the risk of security breaches.
Biometrics
- Biometrics is a method of access control that uses unique physical characteristics, such as fingerprints or facial recognition, to verify the identity of individuals.
- This method is highly secure, as it is difficult for unauthorized users to replicate or fake someone's biometric data.
- Biometrics can provide a more convenient and efficient way for employees to access the network without the need for passwords or keycards.
Two-Factor Authentication
- Two-factor authentication requires users to provide two different types of credentials to access the network, such as a password and a one-time code sent to their mobile device.
- This method adds an extra layer of security by ensuring that even if one set of credentials is compromised, the attacker still needs the second factor to gain access.
- Implementing two-factor authentication can significantly reduce the risk of unauthorized access to the network.
Role-Based Access
- Role-based access control assigns specific roles or permissions to users based on their job responsibilities or position within the organization.
- Users are only granted access to the resources and data necessary for their role, reducing the likelihood of accidental or intentional data breaches.
- This method helps in enforcing the principle of least privilege, where users are only given access to the minimum level of resources required to perform their job functions.
Educating Employees on Network Security

When it comes to securing a smart office network, one of the crucial aspects is educating employees on network security. Employees play a significant role in maintaining the overall security of the network, and raising awareness among them is key to preventing cybersecurity threats.
Strategies for Raising Awareness
Implementing strategies to raise awareness about network security among smart office employees is essential to ensure they understand the risks and best practices. Some effective strategies include:
- Regular Training Sessions: Conduct regular cybersecurity training sessions to educate employees on the importance of network security, common threats, and how to prevent them.
- Email Reminders: Send out periodic email reminders with tips on cybersecurity best practices and updates on potential threats.
- Posters and Infographics: Display posters and infographics around the office that highlight key security measures and encourage employees to follow them.
Cybersecurity Training Programs
There are specific cybersecurity training programs tailored for office staff that can help them understand the importance of network security and how to protect sensitive information. Some examples include:
- Cybersecurity Awareness Training: Interactive training programs that cover topics such as password management, phishing awareness, and data protection.
- Social Engineering Workshops: Workshops that simulate social engineering attacks to help employees recognize and respond to such threats.
- Role-Based Training: Customized training based on employees' roles and access levels within the organization to address specific security concerns.
Role of Employee Awareness
Employee awareness plays a crucial role in maintaining a secure smart office network. When employees are well-informed about network security best practices and potential threats, they are better equipped to identify suspicious activities and take proactive steps to mitigate risks.
By educating employees on network security, organizations can create a culture of cybersecurity awareness that strengthens the overall security posture of the smart office network.
Concluding Remarks
As we conclude our discussion on securing a smart office network, remember that vigilance and proactive measures are crucial in safeguarding your digital workplace. By implementing the best practices Artikeld here, you can create a secure environment for your smart office devices and data, ensuring smooth operations and peace of mind for all stakeholders.
Stay informed, stay secure, and embrace the future of work with confidence.
Expert Answers
What are the potential risks of an unsecured smart office network?
Unsecured smart office networks are vulnerable to cyber attacks, data breaches, and unauthorized access, compromising sensitive information and disrupting operations.
How does encryption help safeguard smart office devices and data?
Encryption ensures that data transmitted between devices is secure and protected from interception, reducing the risk of unauthorized access and data breaches.
What is the significance of network segmentation for IoT device security?
Network segmentation helps isolate IoT devices, limiting their exposure to potential threats and enhancing overall security within a smart office environment.